Wireless networks are everywhere; they are widely available, cheap, and easy to setup. To avoid the hassle of setting up a wired network in my own home, I chose to go wireless. After a day of enjoying this wireless freedom, I began thinking about security. How secure is my wireless network?
I searched the Internet for many days, reading articles, gathering information, and participating on message boards and forums. I soon came to the realization that the best way for me to understand the security of my wireless network would be to test it myself. Many sources said it was easy, few said it was hard.
How a wireless network works
A wireless local area network (WLAN) is the linking of 2 or more computers with Network Interface Cards (NICs) through a technology based on radio waves. All devices that can connect to a wireless network are known as stations. Stations can be access points (APs), or clients.
Access points are base stations for the wireless network. They receive and transmit information for the clients to communicate with.
The set of all stations that communicate with each other is referred to as the Basic Service Set (BSS). Every BSS has an Identification known as a BSSID, also known as the MAC address, which is a unique identifier that is associated with every NIC.
For any client to join a WLAN, it should know the SSID of the WLAN; therefore, the access points typically broadcast their SSID to let the clients know that an AP is in range.
Data streams, known as packets, are sent between the Access Point, and it’s clients. You need no physical access to the network or its wires to pick up these packets, just the right tools. It is with the transmission of these packets that pose the largest security threat to any wireless network.
Wireless Encryption
The majority of home and small business networks are encrypted using the two most popular methods:
- WEP
- WPA
WEP – Wired Equivalent Privacy – comes in 3 different key lengths: 64, 128, and 256 bits, known as WEP 64, WEP 128, and WEP 256 respectively. WEP provides a casual level of security but is more compatible with older devices; therefore, it is still used quite extensively. Each WEP key contains a 24 bit Initialization Vector (IV), and a user-defined or automatically generated key; for instance, WEP 128 is a combination of the 24 bit IV and a user entered 26 digit hex key. ((26*4)+24=128)
WEP also comes in WEP2 and WEP+, which are not as common and still as vulnerable as the standard WEP encryption.
WPA – WiFi Protected Access – comes in WPA and WPA2, and was created to resolve several issues found in WEP. Both provide you with good security; however, they are not compatible with older devices and therefore not used as widely. WPA was designed to distribute different keys to each client; however, it is still widely used in a (not as secure) pre-shared key (PSK) mode, in which every client has the same passphrase.
To fully utilize WPA, a user would need an 802.1x authentication server, which small businesses and typical home users simply cannot afford. WPA utilizes a 48 bit Initialization Vector (IV), twice the size of WEP, which combined with other WEP fixes, allows substantially greater security over WEP.
Packets and IVs
It’s all in the packets. The bottom line is – while you may be able to employ several security features on your WLAN – anything you broadcast over the air can be intercepted, and could be used to compromise the security on your network. If that frightens you, start stringing wires throughout your home.
Every encrypted packet contains a 24 or 48 bit IV, depending on the type of encryption used. Since the pre-shared key is static and could be easily obtained, the purpose of the IV is to encrypt each packet with a different key. For example, to avoid a duplicate encryption key in every packet sent, the IV is constantly changing. The IV must be known to the client that received the encrypted packet in order to decrypt it; therefore, it is sent in plaintext.
The problem with this method is that the Initialization Vectors are not always the same. In theory, if every IV was different, it would be nearly impossible to obtain the network key; this is not the case. WEP comes with a 24 bit IV; therefore, giving the encryption 16 million unique values that can be used. This may sound like a large number, but when it comes to busy network traffic, it’s not.
Every IV is not different; and this is where the issues arise. Network hackers know that all the keys used to encrypt packets are related by a known IV (since the user entered WEP part of the key is rarely changed); therefore, the only change in the key is 24 bits. Since the IV is randomly chosen, there is a 50% probability that the same IV will repeat after just 5,000 packets; this is known as a collision.
If a hacker knows the content of one packet, he can use the collision to view the contents of the other packet. If enough packets are collected with IV matches, your network’s security can be compromised.
The Setup
My wireless network was powered by a Linksys WRT54G v6 wireless router; It is well known that this model is the most widely used wireless router. Out of the box, the Linksys router came with 1 CD which was nothing more than a visual step by step, what you should do to connect it.
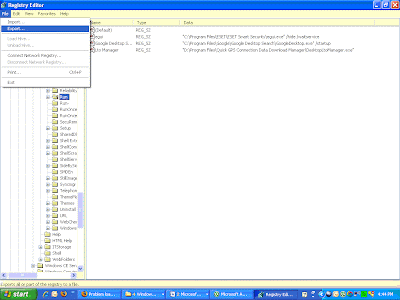
A few things concern me with this router. There was no part in the setup that allowed me, or even told me to change my router’s default password. To change the password, I had to go into the router’s web-based setup utility; this was accessible via the IP address 192.168.1.1 in my Internet browser. The default username and password was
admin. If someone was able to compromise the security on my network, they could have easily done this for me; and locked me out of my own network. Sure, I could have performed a hard reset on the router, but I’d have little luck without the Internet or any documentation to help.
If you’re looking to find your default username and password, there is quite a comprehensive list located at
http://www.phenoelit.de/ My advice is to change this immediately, for it may save you some trouble down the road.
Being my first time, I decided to go easy; I set my router up with a basic WEP 64 encryption; it required a 10 digit hex key. I entered the key into the 2 other computers in my home, and I was ready to start.
Hardware
Out of everything I’ve experienced over the last couple weeks, this was the hardest obstacle, by far. I started with a Dell Latitude C610 notebook with a Linksys WPC54GS Wireless-G notebook adapter (Broadcom chipset) running Windows XP Pro; looking back, it was a bad choice.
When selecting hardware, be warned, not all network cards are the equal. It turns out that nearly 99% of the software used to crack network keys are not compatible with notebook cards that have a Broadcom chipset; the ones that were just didn’t work.
9 out of every 10 articles I read boasted the Orinoco Gold PCMCIA network card by Lucent was the absolute best pick and most compatible will all the good software. A trip to E-Bay, $30 later, and I was ready.
The software we will be using is strictly dependent on the chipset of the WNIC, and unfortunately, the operating system. Your best approach would be to research what software you will be using, and then find a card based on the chipset the software is compatible with.
There are many types of chipsets; too many, in fact, to mention.
Linux-wlan.org has an unbelievably comprehensive list of WNICs and their corresponding chipset.
All the best programs are made for Linux; windows is certainly a drag when it comes to WLAN penetrating software, but if you don’t have Linux, don’t be too concerned.
It may be in your best interest to invest in a wireless card that has an external antenna jack. The Orinoco Gold WNIC I purchased has one, but since I’m compromising my own network in a short range, it won’t be necessary.
The Software
There are hundreds of applications you can use to do a variety of things with wireless networks. The largest list of software, that I came across, can be found at
Wardrive.net. The term “wardriving” is more commonly used for this practice, and involves driving around neighborhoods to look for wireless networks. I refuse to use this term because that is not what I am doing; I am sitting in my home testing the vulnerabilities of my own network.
Let it be known, that it is not illegal to use software to detect the presence of wireless networks; however, if you crack the network and start “stealing” bandwidth, you could be in a world of trouble. Especially if you’re in
Singapore.
Once I received my Orinoco card, I began re-installing software which did not previously work with my Linksys card. It was a nightmare; Windows XP kept getting in the way, software that had been moded to run on windows required daunting tasks for installation, some programs simply didn’t work, some required special run time modules to be installed.
After nearly 48 hours of time-wasting, aggravating, disappointment; I came across the answer. A small penguin shone a beam of light upon my browser and blessed me; I found
Auditor.
(2/6/07 - The link is currently not working, but you can obtain Auditor through any Torrent service.)
Auditor Security Collection is a self booting Linux-based CD that comes pre-loaded with all the best security software for auditing a system. It comes in a .ISO file that can be downloaded from
remote-exploit.org; the ISO image file is roughly 649 Mb, and can be burned to a CD or DVD using most CD/DVD writing utilities.
It was truly amazing; a simple check in the Bios of the laptop to set the boot order to CD/DVD first, a slip of the Auditor CD, and a press of the power button was all it took. I was ready. Be not afraid of this Linux-based CD; everything is laid out on a GUI and all commands have “shortcuts” linking to them on a desktop similar to a windows environment.
Auditor Security Collection does not touch a single file on your hard drive. All files used and saved in the ASC are stored in your notebook’s RAM; once you remove the CD and reboot, everything is exactly as it was.
Detecting my wireless network
If you’ve come this far, believe me, you’re doing well. The first step is to find the network you want to penetrate. As there are a variety of apps that allow you to do this, we will be focusing in on the 2 most popular:
Netstumbler, and
Kismet.
Netstumber - is a widely popular tool used for detecting 802.11a/b/g wireless networks. The latest version is Netstumbler 0.4.0, and will run in Windows XP. For compatible hardware and requirements, you can check the
read me on the Netstumbler forums; or you could just try it. I’d like to point out that many sources have said the Linksys WPC54G/S WNIC does not work with Netstumbler; however, I have been able to make it work by launching the program, then removing and re-inserting the WNIC. The Orinoco Gold works fine with Netstumbler.
Kismet – does a little more than just detecting networks. Aside from providing every detail about a network except the encryption key, Kismet is a packet sniffer and intrusion detection system; we’ll get into sniffing packets a little later.
For this demonstration, we’ll be using the pre-loaded Kismet on the Auditor Security Collection. After inserting and booting the Auditor CD, I was ready to make sure everything was working properly.
From this point, the first thing that needed to be done was to ensure the wireless card was recognized by Auditor; to do this, you will have to venture into the dark world of the command prompt. In Auditor, the command prompt can be reached by clicking on the little black monitor icon located at the bottom of your screen.
Simply typing in
iwconfig will allow you to see all the wireless extensions configured on the machine. If you see a screen full of data next to a WLAN0 or ETH0, you’re ready to continue to the next step; otherwise, you will see a list of “no wireless extensions” messages.
Next, you will need to start the Kismet program. You’ll initially be prompted to enter a destination to save data to; you can just select the ’desktop’ and continue. When Kismet loads, you will see a black screen with green text showing all the wireless networks within you signal range.
Kismet will give you all the information you need to start cracking. Pressing ‘s’ on your keyboard will bring up a ”Sort Network” dialogue box. From there you can press any of the desired sorting methods. This step is important as it allows you to select a particular wireless network on a list to view more details. Select your network with the arrow keys and press enter.
You will then be looking at nearly all your network details such as name, ssid, server IP, bssid, etc… Most are not relevant in this case, but you should write down a few things:
- BSSID
- Channel #
- Encryption method
Pressing ‘x’ in Kismet will return you to the previous screen. re-select your target WLAN; then press ‘SHFT+C’ to bring up a list of associated clients to the Access Point. Write down the MAC address of all clients as it will prove useful.
Capturing packets
While you may have not been aware, at this point, Kismet has also been capturing packets. This is the bread and butter of cracking any wireless encryption; without data to process you have nothing.
Capturing packets, also known as packet sniffing, is the process of intercepting and logging traffic passing over a network. As information is sent and received over your wireless network, the software captures every packet to allow you to analyze and decode it.
Capturing network traffic can be a timely process; especially if it is a slow network. With no-one on any computers in my home, I generally capture around 3,000 packets within 5 minutes; with users on the other 2 computers, this number is substantially greater. Don’t get confused, it’s not the packet itself that we want; but rather the IVs in the packets.
The programs we will be using to sniff packets are
Kismet and Airodump (part of the Aircrack Suite). We’ve already touched Kismet, so lets take a look at Airodump.
Before running Airodump, you must configure your wireless interface to go into ’monitor’ mode; the methods to achieve this require you to go back to the command prompt (konsole).
For most WNICs, you would use the command:
iwconfig <interface> mode monitor
And in some instances would have to set the channel number on your WNIC to match that of the target access point:
iwconfig <interface> channel #
Note that you will have to replace <interface> with the network interface specific to your machine. Using an Orinoco Gold card, my network interface was
eth0; but on most machines, it is
wlan0 or
ath0. So you may have to adjust those commands accordingly. You can find out for sure by simply typing
iwconfig.
I should also point out that putting the Orinoco Gold card in ‘monitor’ mode had a different command altogether:
iwpriv eth0 monitor 2 1
Once your in monitor mode, you’re ready to run Airodump. The command used to start Airodump is:
airodump <interface> <output filename> [mac filter]
<output filename> can be anything you wish; Airodump will put a .cap extension on the end of the name. The mac filter is used to only capture packets from a specific access point. For instance, I used:
airodump eth0 george 00:18:f8:65:fe:41to capture packets just from my access point - where 00:18:f8:65:fe:41 is the BSSID of the AP.
Airodump looks similar to Kismet, but there are no selectable objects on the screen; it gets right down to it, capturing packets and storing them in the .cap file as defined in the command. You’ll notice Airodump keeps a running count of all the packets captured, and better yet, shows you the number of IVs collected.
The waiting game
The hard truth is that you will need to collect nearly 150,000 IVs to crack a 64 bit WEP key, and around 600,000 IVs to crack a 128 bit WEP key. This number varies, but is mostly dependent on how luck you are. If you watch the IV count in Airodump, you’ll notice that, under normal circumstances, they do not rise rapidly.
This can cause a problem; particularly if you’re as impatient as I am. Let’s take a look at some ways we can speed up this process.
Until now, we’ve been using a method known as a passive attack. A passive attack is basically doing nothing other than passively capturing packets until you have achieved enough data to perform the crack.
Most access points need their client to re-associate after a certain period of time to confirm their connection; therefore, the AP will send out an Address Resolution Protocol (ARP) packet. The ARP packet is unique in that is always addressed to the MAC address FF:FF:FF:FF:FF:FF, usually has a size of 68 bytes, and has the ToDS flag set.
We can use this information to implement an ARP replay attack. For this method, we will be using Aireplay (part of the Aircrack Suite). Aireplay can be used to actually re-send packets that it has received.
Leave Airodump running, and open a new command window. The command we’ll be using for Aireplay is:
aireplay -i -m 68 -n 68 -d ff:ff:ff:ff:ff:ff -b 00:18:f8:65:fe:41 eth0
The
-i tells Aireplay to capture packets on the fly; the
-m 68 and
-n 68 tells aireplay that you only want it to replay packets that are 68 bytes. The
-d and
-b are the destination MAC address and AP MAC Address(BSSID) respectively. This is the criteria that is defined for our ARP packet, which is usually associated with an IV.
Alternatively, you may have already captured one of these packets. You can have Aireplay check the .cap file from Airodump with the -f switch:
aireplay -f george.cap -m 68 -n 68 -d ff:ff:ff:ff:ff:ff -b 00:18:f8:65:fe:41 eth0
In either case, If Aireplay finds a match to our specifications, it will show you the details of the packet and ask if you would like to replay it. If the details look exactly as shown below, press ‘y’ for yes.
FromDS = 0, ToDS = 1
BSSID = <mac address of access point>
Src. MAC = <client MAC>
Dst. MAC = ff:ff:ff:ff:ff:ff
Aireplay will then begin to replay the packet; if you’ve found a winning packet, you will notice your packet and IV count in Airodump rise extremely quick. If not, only the packet count in Airodump will rise; If this be the case, press CTRL+C to abort the operation, restart aireplay, and try again.
It has been noted that some routers will detect this erratic behavior and block the MAC address of the WNIC you are using. Adding a -x switch followed by a “replay per second #” will slow down the rate at which Airplay replays these packets.
If your lucky enough, you will have collected enough IVs in little time. For me, it took 28 minutes including booting up, writing down the network specs, and typing all those lengthy commands.
There are other methods such as Dueth attacks which force the clients off the AP, causing them to have to re-associate; but these methods require a second computer.
The crack
Two of the most popular programs used for actually cracking the WEP key are Airsnort and Aircrack. Airsnort can be used with the .dump files that Kismet provides; and Aircrack can be used with the .cap files that Airodump provides.
Airsnort can be used on it’s own without any other software capturing packets; although, it has been reported to be extremely unstable in this state, and you should probably not chance loosing all your captured data. A better method would be to let Airsnort recover the encryption key from your Kismet .dump file. Kismet and Airsnort can run simultaneously.
For this demonstration, we’ll be using Aircrack. You can use Airodump to capture the packets, and Aircrack to crack the encryption key at the same time.
With Airodump running, open a new command window and type:
aircrack -f 3 -n 64 -q 3 george.cap
The
-f switch followed by a number is the fudgefactor; which is a variable that the program uses to define how thoroughly it scans the .cap file. A larger number will give you a better chance of finding the key, but will usually take longer. The default is 2.
The
-n switch followed by 64 represents that you are trying to crack a WEP 64 key. I knew because it was a setup; In the real world there is no way to determine what WEP key length a target access point is using. You may have to try both 64 and 128.
The
-q 3 switch was used to display the progress of the software. It can be left out altogether to provide a faster crack; although, if you’ve obtained enough unique IVs, you should not be waiting more than a couple minutes.
A
-m switch can be used, followed by a MAC address, to filter a specific AP’s usable packets; this would come in handy if you were collecting packets from multiple APs in Airodump.
Aircrack recovered my WEP 64 key within 1 minute using 76,000 unique IVs; the whole process took around 34 minutes.
The same experiment was repeated with WEP 128 and it took about 43 minutes. The reason it was not substantially longer is because I simply let Airplay replay more packets. Sometimes you can get lucky and capture an ARP Request packet within a few minutes; otherwise, it could take a couple hours.
After I had access to the network, many doors opened up. Aside from having access to the Internet, I was able to use
Networkview – a network discovery tool – to obtain my network’s workgroup name. From there, I had access to all the shared files on my drives.
While I’m no expert in the subject, I can at least assume that many horrible things could happen if the wrong hands were to obtain my WLAN encryption key.
The conclusion
Always use WPA or WPA2 encryption when possible. If your using WPA with a pre-shared key, use a strong password; hackers can use dictionary attacks, and they will be quite effective if you have an easy password. You may want to use a strong password generator like the one at
grc.com.
If your access point supports it, you may want to consider disabling wireless SSID broadcast; however, this may raise some issues with the APs clients recognizing it. (Kismet will still recognize it)
Many routers will allow you to filter what clients can access the network; this is known as Wireless MAC Filtering. If you know the MAC address of the clients you are using, you can enter them into your configuration utility as “Permit ONLY”. This is not a 100% effective method; MAC addresses can be cloned to match the AP’s associated clients, but it does provide you with a slightly higher level of security. (there is a utility on Auditor to allow you to do this)
By default, your router may be set to mixed mode; this allows 802.11b and 802.11g devices to access your network. If you use only 802.11g devices, set your router to G-ONLY. Had my router been set this way, I would have never been able to do any of this. The Orinoco Gold card is 802.11b, and is obviously not compatible with a 802.11g network. Many 802.11g cards are not supported by the software we’ve used in this tutorial, but few are. While your at it, please change your default router username and password.
While I haven’t tried my hand at cracking a WPA encryption, the methods are similar when the WLANs use pre-shared keys (psk); I do plan on trying it, and I will surely write an update to let you know how/if it was done.
By no means am I claiming to be an expert in this field; If you’ve noticed anything that was incorrect or just have something to add, please feel free to drop a comment.